Custom Permissions on Models
If you require more flexibility, you can implement a custom permission policy. Each role can have its own permission policy or you can share an implementation across several roles. One common example involves hierarchical data structures such as corporate organization charts. A corporate division may want to create a role for division personnel to report against subordinate sites, which may themselves have subordinate reporting organizations. In these cases, it's appropriate for the division level personnel to see information relevant to its subordinate organizations all the way down the org chart, but not be able to see other division's data. In these cases, you can create a custom permissions policy class in Java.
Procedure 4.3. To use a custom permissions policy
Create a class that implements the interface com.onenetwork.platform.data.model.CustomModelPermissionPolicy .
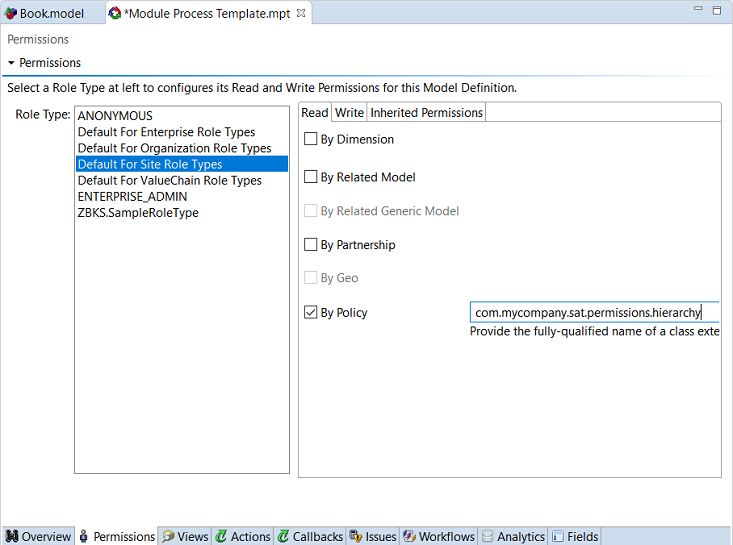
Click the custom permissions policy checkbox.
Enter the fully-qualified class name.
Figure 4.2. Custom Permissions Policy is set by selecting the checkbox and typing the full class name of the permissions policy class you created.
You must still give the role permission at the action, issue, and view level if applicable.
The CustomModelPermissionPolicy interface implemented has three methods. ThegetReportPermissionQueryContribution and getViewPermissionQueryContribution methods are used for read operations, while applyCustomWritePermissions is used for write operations.
Here is an example of creating a custom permissions class. This particular example implements only View permissions, but more often you would implement all 3 methods.
public class MyPolicy implements CustomModelPermissionPolicy { @Override public void applyCustomWritePermissions(ActionPermissionRequest req) { } @Override public PermissionQueryContribution getReportPermissionQueryContribution(ReportPermissionRequest req) { return null; } @Override public PermissionQueryContribution getViewPermissionQueryContribution(ViewPermissionRequest req) { if (req.getPlatformUserContext().getRoleTypeName().equals("PCTA.SampleRoleType")) { PermissionQueryContribution contrib = new PermissionQueryContribution("STR_FIELD != 'NOT_ALLOWED' and $MY_ENT_NAME$ = 'SampleEnterprise' and $MY_VC_ID$ = 9655"); return contrib; } return null; }}